Saturday, December 15, 2007
News 15 - Ethical Issues on Facebook - Beacon Controversy
2. Here is a link to an interesting article about the social networking website Facebook and ethical issues on tracking and reporting of user data:
http://www.pcworld.com/businesscenter/article/140372/wakeup_call_in_facebookbeacon_controversy.html
3. The author of this article is reporting on the outrage that many people felt at Facebook's use of the Beacon program to track transactions of its users on third party website linked to Facebook and then reporting this information to friends of the user on their Facebook homepages. The questions that the article poses relates to the Privacy, Accuracy, Property, Accessibility issues that classmate Freda Thomas discusses in her blog entry:
http://bb.bbprod.cuny.edu/webapps/portal/frameset.jsp?tab=courses&url=/bin/common/course.pl?course_id=_19305_1
Privacy, property, and accessibility are definitely issues in the Facebook-Beacon controversy. Was this program a breach of privacy? Is the information obtained from tracking the activity of the Facebook user the property of Facebook since the user consented to join the social networking website? Should other users of facebook be allowed to access this private information? Does facebook have a right to track and distribute users' personal information? I believe the outrage that resulted from this incident and the apology from Facebook's CEO tells us that the answers to these questions are no. Companies need to reevaluate their code of ethics and be stricter in enforcing them. Use of information that can directly compromise the customer is neither right nor good for business in the long run. Yet many companies have continued these business practices, acting radically on personal information they have collected for quick profits.
Saturday, December 8, 2007
News 14 - Web Based vs Face to Face Negotiation

2. Below is a link to an article that discusses collaborative software as a way for a group of people to negotiate and reach a decision together:
http://ross.typepad.com/blog/2003/08/negotiation_and.html
3. The author states that collaborative software such as Socialtext is a good way for people to negotiate because preferences are revealed for all to see. He compares this experience to negotiating in person, which the author believes is inferior to negotiating through this internet based platform. The reason is that in a face to face setting, personality can inhibit effective negotiation.
A fair negotiation should be based on understanding and equal distribution of benefits to the involved parties' and should not depend on personality. However, personality can often help to arrive at a decision more quickly, especially if one side presents a stronger argument and is better at obtaining his/her objectives than the opposing side. I think that the outcome of a negotiation is not necessarily fair - one party may benefit more than the other. The only condition is that both parties must be sufficiently satisfied with the outcome to reach a common decision and to possibly collaborate again in the future for mutual benefit.
Indiv 5 - Negotiation

1. Our group made decisions by sharing our value information through email and then analyzing the information via excel to come up with a decision that is relatively good for everybody involved.
2. I found that in the process of a negotiation, people with different objectives must compromise to reach a solution that all parties involved agrees to. Often sacrifices need to be made by the individuals, some greater than the others, in order to reach a decision. Another problem is that often when parties negotiate, they may not trust each other because they are not entirely clear of the others' objectives.
3. I believe that we our decision-making process was similar in fashion to those of the rest of the class because we do not require or have access to many resources to help us make this negotiation process easier. However, since this is a simple negotiation experiment, we do not need special software to aid us in this process.
4. For a complex negotiation involving many companies, a more organized approach should be used. An internet based application can be used to help people negotiate and reach a decision. One example of such a software is smartsettle.com. Smartsettle.com is a secure web platform that allows companies and individuals to analyze their preferences, negotiate, and reach a decision in real-time. This service makes the negotiation process quicker and easier.
Links:
http://mediationblog.blogspot.com/2006/10/high-resolution-new-negotiation.html
http://www.smartsettle.com/html/advantages.html
Saturday, December 1, 2007
News 13 - Systems Development Life Cycle
2. I found an interesting article on this topic. http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=71151&pageNumber=1
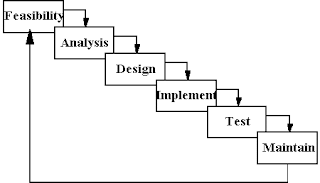
3. The author believes that the problem with the waterfall model is that the waterfall model assumes that the only role for users is in specifying requirements, and that all requirements can be specified in advance. He explains that the requirements always grows, and change on design and development must be made. Feedback and interactive consultation will be very helpful. Therefore, many other SDLC models have been developed, such as, the fountain model which considers overlap of activities throughout the development cycle, and the spiral model which emphasizes the need to go back and reiterate earlier stages a number of times as the project progresses.
I agree with the author’s point of view. A single waterfall cycle is not enough to create a sufficient system because in a complex system, the developers can’t do all the analysis and get everything right without doing any design or implementation. The developer needs to do some analysis, then some design, then some implementation, and then go back to the cycle to do more analysis. In this way, the developer can refine the system, and eliminate constructive errors.
Saturday, November 24, 2007
News 12 - Cable vs. Telco
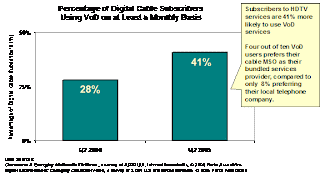
2. http://www.businessweek.com/investor/content/oct2007/pi20071010_242433.htm?chan=search
3. I think this article sums up the competitive situation of the cable and telecom companies very well. Each is integrating into their companies the services traditionally provided by the other. Cable have implemented and increased their voice services and video services, whereas telecommunications companies are becoming less dependent on wired-line phone business and offering more on wireless and DSL and video service. Companies such as Verizon are investing in FIOS technology in order to compete with cable companies on video and other services that require high bandwidth. I think the article would be more complete if it were to propose the use of different emerging technologies in the future and estimate how this will affect the companies financially, similar to what we have been doing in class.
Saturday, November 17, 2007
News 11 - Zagat Survey on Physicians

2. Attached is a commentary on the Zagat Survey for Physicians:
http://www.healthbeatblog.org/2007/10/the-pitfalls-of.html
3. The article comments on dangers of rating physicians the same way as restaurants are rated.The author suggests a comparable experience, "It’s a bit like having car ratings only address color scheme and seat comfort: these are nice facts to know, but at the end of the day you want a car that you can rely on, a consistent performer that does its job and does it well."
Indiv 4 - Information Aggregation Through Electronic Market
 1. There are two other types of business that might use the information aggregation method. An international freight forwarding company needs to collect information to predict the currency exchange rate. International trades are highly influenced by currency exchange rates. For example, if the exchange rate between US dollars to Canadian dollars decreases, US import from Canada will also decrease, but US export to Canada will increase. Therefore, international freight forwarders need to predict the rate for their business planning. They can use this method to collect currency rate prediction from the currency trading brokers.
1. There are two other types of business that might use the information aggregation method. An international freight forwarding company needs to collect information to predict the currency exchange rate. International trades are highly influenced by currency exchange rates. For example, if the exchange rate between US dollars to Canadian dollars decreases, US import from Canada will also decrease, but US export to Canada will increase. Therefore, international freight forwarders need to predict the rate for their business planning. They can use this method to collect currency rate prediction from the currency trading brokers.The airline industry can also benefit from this method by collecting information to predict the future fuel price. Airlines need to sell tickets for flights in the future. Since fuel price fluctuates, the ticket price should also be adjusted. Airlines should collect information from the electronic market, and predict the future fuel price.
2. There are problems in this method besides the ones mentioned in the background information section. First of all, this method does not prevent or consider sudden catastrophic events that might suddenly crash the market. Second of all, each participant has its own predication on the market, but sometimes, it is only their personal beliefs. Even though the majority of participants might prefer one result in the market, but it is not a systematic analysis. Therefore, it might not be reliable.
3. An online trading system is a good enough for this practice. The company can setup a web server. It should contain account information of each participant, and allows them to trade on this electronic market on the website. Participants can trade on currency, fuel, or stocks depending on the company’s objective.
Saturday, November 10, 2007
News 10 - OpenSocial
2. Related article: http://www.techcrunch.com/2007/10/30/details-revealed-google-opensocial-to-be-common-apis-for-building-social-apps/
3. The article is about Google's launch of a standardized platform for developing applications for social networking websites, called OpenSocial. It features many participants, called hosts, that feature user data and content. Developers then use this standard to create software for the social networking sites. To my surprise, many hosts, such as MySpace, Friendster, LinkedIn, have already agreed to this. The OpenSocial platform promises to make more varied types of applications compatible with all host social networking site, making distribution easier for developers of software applications. I agree with the author that the success of this new OpenSocial platform would make life easier for software developers. Traditionally different websites use different programming languages, and the developers need to use the same language that the websites use. Now OpenSocial can provide the connection between the developers' application program to the social websites. The developers can use any computer language for thier application, and they will be able to access the data from the social websites through OpenSocial. Therefore, OpenSocial enriches the users of these websites by making more variety of applications available to them.
Saturday, November 3, 2007
News 9 - AT&T Will Bid in Wireless Auction
Another type of auction is the Dutch clock auction. The high price is set by the seller. The offer price then decreases at fixed amounts until the first bidder to take the offered price and agrees to buy the item.
2. AT&T will bid for more wireless spectrum:
http://www.pcworld.com/businesscenter/article/138687/att_will_bid_in_wireless_auction.html
3. In the article, the author discusses AT&T uncertainty of whether it should bid for wireless spectrum on the 700 MHz band due to complex conditions of sale set by the FCC. The FCC requires the winning bidder to open access to all wireless devices for certain bands of spectrum.
Many believe that there will be much competition in the auction for parts of the wireless spectrum capable of providing high speed data service. According to recent news, prices offered to buy spectrum are at record highs. In addition to telecom companies, internet companies such as Google are trying to enter the scene, as well as Apple, a computer and multimedia company.
In my opinion, AT&T probably has already made a decision regarding acquisition of more of the coveted spectrum. I believe that it is possible that they are purposely keeping bidding information discreet because it is advantageous for bidders to reveal as little information as possible to other bidders prior to bidding for an item to increase their chances of winning in this type of auction.
Saturday, October 27, 2007
Indiv 3 - Walmart's and Dell's Successful Strategy

I agree that Dell's and Walmart’s advantage over their competition is not due to technology, but due to management. Their success is not coming from advanced technology.
For nearly five decades, Wal-Mart's has provided low-priced products to its customers. Wal-Mart does not have any special advantage in technology. Wal-Mart stores operate according to their "Everyday Low Price" philosophy. It mainly has advantage over its competitors because it has been better at containing its costs.
Dell is in a similar situation as Wal-Mart. Dell makes low-end computers, and does not use particularly advanced technology in comparison to its peers. Dell’s success lies mostly in its supply chain management, which enables the company to lower down its cost.
However, recently both companies have been experiencing problems because they have been sacrificing product quality in order to achieve lower costs. Walmart forces its suppliers to compete with each other to reduce their wholesale prices. The supplier then will turn back the loss to the manufacturer, which results in bad product quality. Eventually, this will affect consumers’ confidence on Walmart’s products.
Dell is facing the same problem. Outsourcing customer service and producing products overseas is causing a loss in confidence in their products and services.
News 8 - P&G Supply Chain Management Solution
2. I found a recent news article related to Supply Chain Management
http://www.scmr.com/article/CA6494820.html?industryid=48314
3. The article is about Proctor & Gamble’s decsion to choose Optiant software to help implement its new supply chain strategy. The Optiant SCM software will help P&G deliver their products to customers in the most efficient manner. In order to fulfill its inventory planning and optimization goals, P&G is looking forward to expanding the partnership with Optiant.
I agreed with P&G’s business idea because a good SCM provides optimal coummication and control over vendor, customers, warehouse and transporation. Instead of spending money to develop its own SCM software, it is better to outsource the SCM to a professional supply chain solution company, such as Optiant, because they are more experienced in this area. This will allow P&G to focus on the bigger picture of their business. In the new age, businesses will be able to receive or make orders, ship products, check inventories, pay vendors and bill customers through the SCM system without the need to step out of the office or make any paper transactions.
Saturday, October 20, 2007
News 7 - Artificial Intelligence

I found an interesting article about Artificial Intelligence:
http://www.fuchsiashockz.co.uk/articles/artificial_intelligence/supercomputers_key_to_the_brain.php
The article is about a group of scientist trying to use the world’s most powerful supercomputer, Blue Gene, to simulate the human brain’s function. They hope they can find out more about the human brain. However, people are worried that this project will lead to a computer having conscious thought or have a mind of its own. The answer from one of the head of the project, Markus Baertschi, is no. He declares that the brain is still far more complicated than the computer. This supercomputer only has 8000 processors to simulate each individual virtual neuron in the brain, but the human brain has trillions and trillions of neurons. Beside the size difference, scientists still do not know how to make the processors work together like a brain.
I agree with the scientist in this article that it is too early to worry about an artificially created machine life. We should do more research and development on artificial intelligence because we can utilize this technology to help us on many areas, such as, medical, laboratory, industrial and entertaining purposes.
Friday, October 12, 2007
News 6 - eBay and Advertisement
2. Below is an article on the role of online advertising in ebay.com: http://www.pcworld.com/article/id,138155/article.html
3. EBay’s highly successful business model is providing a place where sellers and buyers can process transactions using online auction, generating revenue for eBay. However, eBay’s direction apparently changed recently when it signed a deal with Yahoo and Google to display exclusively their pay-per-click and PPC text ads featuring external retailers. According to the article, this business of online advertising has doubled eBay’s advertising revenue compared to last year, at the expense of drawing a number of customers away from eBay sellers.
I agree with the author that advertising for external retailers may hurt sellers. Sellers are forced to compete with bigger, more well-known retailers. The venture mainly generates more revenue for eBay and other participants, but not eBay sellers. On the other hand, customers benefit from more options. They are able to compare items on eBay with outside retailers’.
In my opinion, this advertising deal is a short-term strategy because it may eventually lead eBay sellers to abandon eBay due to loss of sales. Furthermore, customer traffic drawn to eBay’s system of bidding are distracted and redirected to other sites. These customers may become loyal to outside retailers and abandon eBay completely. Perhaps, we also cannot overlook that traffic to eBay may drop due to repulsion from over-advertising. Thus, eBay may potentially lose on both advertising revenue and eBay sales commissions. On the other hand, these problems may be averted if eBay is able to manage the type and number of ads that can be displayed on the site.
Saturday, October 6, 2007
Indiv 2 - Tracking File Sharing in P2P

1. There are ways for a manager of a P2P network to monitor the type of files that are being shared. The fact that there is news of people who share copyrighted material on P2P being caught and penalized indicates that this is possible.
Two ways the manager of a P2P network can monitor the types of files that are being shared is through a software or website with tracker listed. The file is registered with a server, called tracker, and the tracker keeps track of which seeds and peers are in the network. The seeds are clients with completed files, and the peers are clients with incomplete files. P2P peers can connect and download segments of the files from any seeds and peers from the tracker.
If the P2P network is using a trackless system, (decentralized tracking) every peer acts as a tracker through the distributed hash table (DHT) method. The manager can also monitor the network by the ping monitor method. A ping command is sent to every peer machine within the network using a peer protocol on the peer machine, and it will request a response with DHT info. If a response is received at the sending peer machine, the responding peer machine is operating, and the monitor program will receive the DHT info from each peer machine.
2. I think it is worth tracking because it could help protect copyrights.
3. I believe the monitoring should be paid for by the tracker website and the P2P software provider because they are providing the P2P service and should be liable for tracking any illegal downloads that are occurring on the network.
News 5 - CRM Selection
2. Since there are so many CRM software being marketed out there, I think that companies face a lot of confusion when choosing a suitable CRM system. Here is a link to the article I found giving advice on this topic:
http://www.crm2day.com/library/EEEuukAukEdtvgQDjz.php
3. The author believes that choosing the right CRM system will help the company serve its customers better. He suggests that different CRM decisions should be made by big and small companies. According to the author, there are 10 factors to consider when choosing a suitable CRM system.
I agree with the author’s view that a company has to choose a CRM with functions geared toward achieving the company's goals. All aspects of a business' management should aim to the business' goals, and that includes technology. Also, the new system must be compatible with the current system in order to have a smooth installation. There should not be a chaotic installation period where existing customer service management would be interrupted. It should be reliable throughout and user-friendly. Lastly, extra embedded functions are always a plus. I think the author was thoughtful in considering the factors for a suitable CRM. However, I suggest that he should distinguish the factors in order of increasing importance as the nine factors after the first one appear to be listed in random order.
Saturday, September 29, 2007
News 4 - Database Security
2. This article is about how database security is often overlooked:
http://www.eweek.com/article2/0,1895,2186652,00.asp
3. I agree with the author that security for databases is being overlooked. Recently, there has been news that many major retailers’ customer information has been compromised through hacking into the retailers’ database. In fact, I was one of the people whose credit card was affected by one such incident.
The author attributes this lack of database security to the database administrator’s inability to use sufficient time to meeting database security needs and also to lack of security training. It makes sense for the people who create and maintain these databases to be responsible for controlling access to this information. However, this indicates a more major issue that companies are not allocating enough money or attention to protecting customer’s information. The company should be responsible for hiring people who will be able to protect the information that the company acquires from customers.
The article suggests that a possible solution is to have the database administrator train with the IT security team. However, according to the article, one of the common reasons that the database administrator could not perform the security measures is lack of time. I think the author should explore more possible solutions such as using protective software, using an external database security consulting group, hiring more security savvy workers, or hiring more workers so that sufficient time can be allocated to security measures.
Saturday, September 22, 2007
News 3 - Peer to Peer Network
2. Also, I learned that there are different ways computers can connect to each other to form a network. One is client-server and the other is peer-to-peer. There are also hybrids of the two.
3. http://www.computerworld.com/action/article.do?command=viewArticleBasic&articleId=9009143
4. The article from earlier this year talks about Microsoft’s release of Window’s Vista. Before the version for individuals was released, pirated versions of the software were already available for download using BitTorrent, a peer-to-peer service.
I agree with the author this peer-to-peer file-sharing network is threatening Microsoft’s profit and no amount of consumer education will stop people from using the pirated software. Some readers of the article suggest that Microsoft should lower its prices on the software. Although I believe that it will alleviate the situation, people will still prefer the free version of the software if it is available through BitTorrent. In order for Microsoft to achieve the goal of anti-piracy, it will need technical solutions or to threaten lawsuits to reduce piracy.
BitTorrent is a fast and efficient way for users to exchange files between computers in a network. However, although there has been regulation on peer to peer services in the past, some file sharing networks continually fail to monitor the file-sharing, so there have been many pirated versions of music, video, and now software distributed this way. This technology is beneficial to the users. However, for certain businesses, this is not good because the value of their intellectual property is being chipped away.
Found another interesting article:
http://www.news.com/Congress-P2P-networks-harm-national-security/2100-1029_3-6198585.html
Saturday, September 15, 2007
News 2 - Object Oriented Programming
Machine language is the lowest level of computer language, and it’s all in numbers. It manipulates the computer hardware by instructions translated from assembly language.
Object oriented programming language (OOP) is a high level computer language. The essential characteristic of object oriented language is uses of object. An object is a module that contains one or more routine functions. The programmer can create relationship between one object and another. The new object can inherit the basic functions from the existing object. It increases the reusability and modifiability of the program.
2. I found an interesting article about object oriented programming:
http://www.devx.com/opinion/Article/26776
3. The author in this article believes that OOP is good in theory, but it’s not so good in practice. He thinks OOP leads to programmers not understanding each other’s code. The author suggests that simply copying and pasting codes can replace the OOP’s concept of code reusability.
I don’t agree with the author’s point of view. The ideas of reusability and modifiability must take into consideration the business concept- OOP allows software companies to sell their code packages to another company, or pass the packages to another developer without revealing their codes. There will be security issues if all written objects’ codes were readily accessible by anyone. Also, the author’s idea of copying and pasting codes is not practical because it will generate more errors and compatibility issues. He did not suggest any viable alternative to OOP that would simplify the programming experience and improving efficiency.
Tuesday, September 11, 2007
Indiv 1 - Programs for Actuarial Analysis
There is a client server which the employee can access through a user terminal called Mocha. There are many subprograms here in which I can input or extract data. Access to those subprograms is restricted according to employee’s job function. In addition, the FTP program allows a computer to connect to the client server to download client data into the computer. Using Norton Commander, an orthodox file management program, I can edit certain variables (such as which mortality tables to use) in a data analysis program and then run the programs. The actuarial programs then manipulate and analyze the data files obtained from the client server in a way to serve the purpose. The programs produce useful output which can allow an actuary to draw conclusions about the health of the retirement benefit plan or estimate/predict some events will likely happen in a given plan.
2. Which one do you find most useful and which one least useful?
I would say the most useful programs are the actuarial data manipulation programs which are particular to the actuarial department and which we can edit variables and run through Norton Commander. I find that the least useful program is Norton Commander in that it involves extensive keyboard use.
3. What additional features do you wish that these programs have?
I wish that Norton Commander was more user-friendly so that we can use the mouse to drag and edit the data instead of only being able to use the keyboard.
4. Can these programs be customized by using a computer language? Which one?
I believe the programs can be customized by using an object oriented computer language such as C++.
Saturday, September 8, 2007
News 1 - Apple iphones for IT staff?
1. I learned about different type of computers in class. Specifically, I was interested in what a server was so I looked into it and found that computer servers can control, manage or monitor other computers and devices on the network. Also, that there are other types of servers such as printer servers and web servers.
Another concept I learned from class this week was how a company's website reflects its business strategy. From Dell’s website, I learned that Dell had a conflicting strategy on its website where it was targeting both sophisticated and beginner computer users.
2. I found an interesting article from the internet relating to our class on hardware. This article offers tips about how iphones can be used to help IT staff at work:
http://www.infoworld.com/article/07/07/24/What-to-do-if-the-CEO-gets-an-iPhone_1.html
3. The author implies that companies should provide IT with Apple iphones that work on the company's computer network by suggesting several features of iphone that supports this use. I don't agree this implication because the iphone may be sufficient for personal entertainment, but may not be as suitable as a laptop or desktop would be for IT work. The iphone uses only Mac OS/software applications, is solely compatible with AT&T service, has restrictions on speed, and is more easily hackable. Also, the article does not mention technical plans or specifications for connecting the iphone to a company's network. However, I think an IT manager might still be interested in this article because using new PDA devices in the work environment may be a way to better productivity if the restrictions imposed by use of this particular PDA device could be overcome.